Award-winning digital marketing and creative.



-1.svg)

.svg)
Powered by humans, fuelled by data.
We work with globally ambitious clients in need of greater certainty in a rapidly changing digital landscape. We drive sustained, measured growth through multi-channel digital marketing campaigns across your owned, paid and earned media.
We consistently outperform the market and our unbroken year-on-year award winning streak demonstrates this. Our clients benefit from this unrivalled competitive advantage in their organic and paid search, paid social and content production.
Our strategy is led by data but we are not slaves to it – key decisions are human-powered.
Since 2012, we've thrived on partnering with forward-thinking brands – from rising stars to industry giants – to co-create the future and push the boundaries of innovation.




















Discover how we've helped diverse brands achieve their digital marketing ambitions.
What we do
We engineer full-funnel retail and digital commerce experiences that connect brands with customers, across B2C and B2B landscapes.
Social Media
Social Media
Where culture meets conversion. From scroll-stopping creative to precision paid ads management, we craft social experiences powered by insights and data—turning passive audiences into passionate communities.
Creative
Creative
Full-service creative, built for impact. We expertly blend strategic ideation, standout visuals, video production, and branded storytelling to command attention, spark conversations, and amplify your brand story.
SEO
SEO
.svg)
Visibility, amplified. Pairing a data-led approach with content fluency to build long-term, compounding growth. Agile, adaptive, and always performance-driven.
Strategy
Strategy
.svg)
.svg)
One brain, many perspectives, no guesswork. We craft strategies that blend human ingenuity with insightful analytics, ensuring clear paths forward through even the most complex challenges.
Paid Media
Paid Media

.svg)
Built for scale, optimised for nuance. Our approach fuses platform mastery with relentless experimentation to deliver high-converting campaigns—measured, meaningful, and margin-smart.
Websites
Websites
Part brand, part engine. We design and build high-performance sites that don’t just look beautiful—they accelerate journeys, convert visitors, and scale with ambition.

We are a pioneering digital marketing agency, fundamentally operating through our unique, signature 'one brain' philosophy. This synergistic approach seamlessly merges advanced analytical capabilities with diverse human perspectives, bridging the gap between what's possible and what's delivered.
The power emerges from every part working together to achieve more than the sum of its parts, delivering unparalleled efficiency and deeper audience understanding. It’s this unified mindset that sets us apart—one agency, one strategy, built to drive clarity, consistency, and unmatched performance.
From shaping strategy to executing across channels, we transform complexity into results, amplifying your existing capabilities and helping brands move with purpose and grow with confidence in an ever-changing digital landscape.
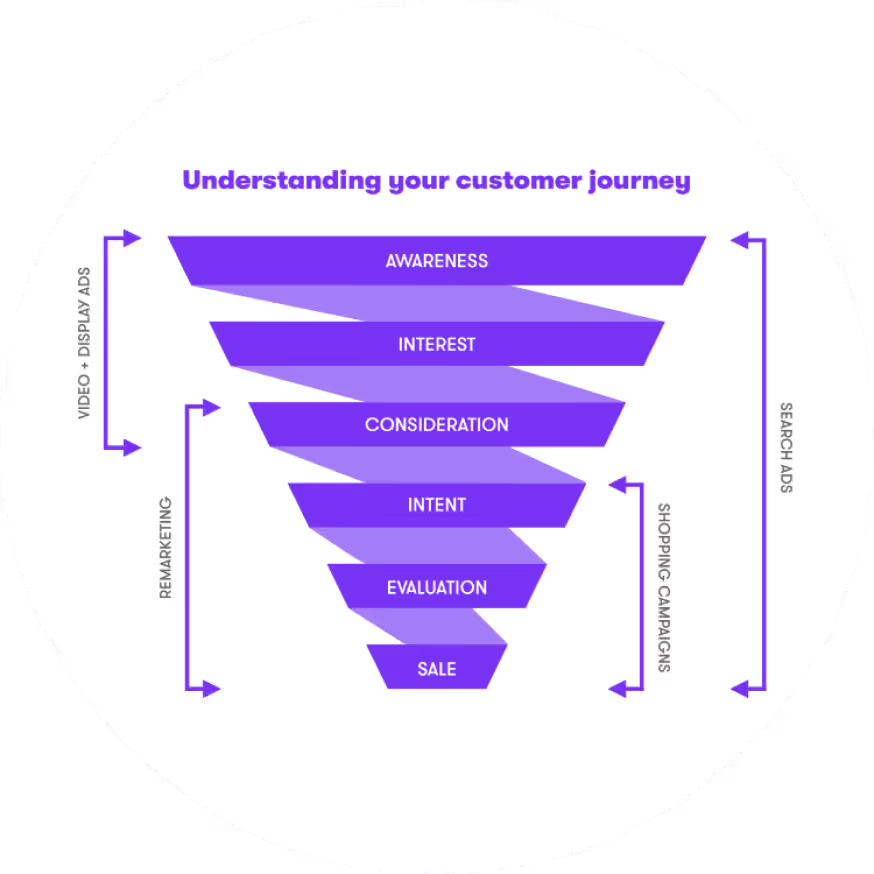
Focusing on a single channel, can at times lead to tunnel vision and missed opportunities. At Clearwater, we craft integrated strategies that mirror real-world digital behaviour—where audiences move fluidly across SEO, SEM, Social Media, CRO, Web, email, and beyond.
A multi-channel approach meets customers in multiple moments, aligns messaging at every touchpoint, and extracts greater value from every dollar spent. It’s not about doing more—it’s about doing what’s most effective, holistically.
By strategically allocating your budget across owned, paid, and earned media, we build momentum, drive sustained performance, and ensure no valuable interaction is left untapped. That’s marketing with purpose.
Our campaigns don’t just perform—they set benchmarks. With a multi-year streak of global awards, we’re proud to be recognised for the impact we create and the standard we uphold.






Creative design bolsters everything we do.
Get in touch
We’d love to hear about your needs.

Common questions we get
Common questions we get
Digital marketing is a broad term used to cover all efforts designed and implemented to increase awareness, interest, and consideration of your brand across online platforms and devices connected to the internet. This means a targeted mix of campaigns across websites, social media platforms, search engines, applications, and a growing number of new, innovative channels set to improve the communication between businesses and their potential customers. The common components of a successful digital marketing campaign is a rigorous strategy built around business objectives, creative content paired with technical expertise, and consistent, transparent reporting and analysis to refine for better performance
Modern business is conducted online, and without a refined, high performing digital presence, it is likely your operations could rapidly fall behind the competition.
Websites, social media accounts and other digital platforms create a convenient way for consumers to search for new products and services, as well as find valuable content to keep them engaged and entertained for hours every day. Businesses across the world are leveraging this fact, and the internet is now filled with flexible, creative channels allowing businesses of all sizes to better target and interact with their ideal audiences in real-time. With this data and a range of sophisticated capabilities available, it also makes marketing more affordable and effective with unlimited reach potential when compared with traditional advertising methods.
When a proper strategy is developed incorporating your specific business objectives and industry features, your business can maximise the appropriate tools available to you to increase return on investment in generating new leads or sales.
Given the large amount of digital marketing channels available, it can be overwhelming to decide which is best to achieve your business’s marketing goals. Simply jumping headfirst into all of them can spread your resources too thin and leave you struggling to see healthy returns. Equally, limiting your efforts to only a corner of the options available can leave a large portion of your potential audience untapped.
The key is to identify your ideal customer and learn where they are spending their time online. In other words, who do you want to purchase your offerings, and where would they most likely be searching for them? This could be through digital media buying, over search engines, specific social media channels, or perhaps they require a more indirect, nurturing content marketing campaign with a constant stream of information across multiple platforms. Every business is different and will require a unique marketing mix to achieve their goals alongside available budgets.
Digital marketing agencies accumulate best practice knowledge and industry insights to deliver greater return on investment for their clients in exchange for a proportional management fee. Creating, analysing, and optimising your own digital marketing campaigns can be near impossible without any experience, but it is important to ensure ROI is front of mind with your efforts. Hiring a digital agency is the common solution for many, however it is crucial to select a reliable provider to place your business in the best stead with your campaign performance.
At Clearwater, our team ensures you are consistently receiving the full range of services owed to you, from initial consultation and strategy development, to expert campaign creation with professional resources and funnel considerations, and transparent reporting and analysis to refine campaigns for greater ROI.
Digital marketing campaigns perform best when they are erected around a marketing funnel model. This can get quite technical, but essentially a funnel works towards structuring digital marketing efforts attracting as many people as possible within a target audience, building their engagement, and nurturing them towards completing a specific sale or objective. We do this by tailoring campaigns and content created within them to build brand awareness, pique the interest and spark consideration of your offerings within that audience, and then continuously deliver frictionless, high-performing customer experience until they are ready to make a purchase, submit an enquiry, or complete another task you desire from them
Given the versatility of digital marketing campaigns and the myriad goals they are trying to accomplish, the time it takes to see results will naturally vary. For example, search engine optimisation (SEO) is a long-term investment requiring patience and refinement before exponential benefits can be achieved. Paid digital marketing campaigns, however, such as Google Ads or Social Media Advertising, can use the consumer insights and keywords captured by the respective platform to deliver more immediate results from your campaigns. Depending on your industry competition, individual business goals and available resources, results can range from being achieved in a matter of hours, days, weeks, or months. The differentiating factor will be the skill at which a campaign is delivered.
Clearwater Agency is an Australian owned and operated, providing digital services to Australian businesses, large and small. We are based in Melbourne and work with businesses Australia wide, including Sydney, Brisbane, Perth, Adelaide and Hobart.
Clearwater brings together a range of specialists in not just every discipline of digital marketing, but also in terms of industry knowledge. We take the time to understand your specific situation and objectives, and have the expertise and resources to build you a tailored digital marketing strategy that employs the appropriate tools, platforms and metrics to deliver you the best return on investment as soon as possible.
Clearwater will partner with you to translate your digital goals and objectives into business growth and online success. Our agency’s philosophy is simple. We want to understand your business, your goals, your customers and audience, as well as you do.
Our commitment is to become an integral part of your business and a trusted and valued partner. Our digital marketing agency is outcome based, not service lead, resulting in the right channels, platforms and approach for your business.
Our Melbourne based digital marketing agency is committed to delivering transformative digital marketing performance and management for our clients and partners. Digital success starts with a plan, a vision, and the capability, focus and commitment of a team that can bring it to life. Speak to one of our strategists and find out how.









.png)





